First CONCORDIA Workshop on Collaborative DDoS Mitigation
TL;DR
What? A workshop with the goal of bringing together DDoS research and operations, learn from each other, and discuss
advancements in the field of collaborative DDoS mitigation
When? September 15th, 2022. With a drinks and networking event the afternoon / evening before (Sep 14)
Where? Villa Jongerius, Utrecht, The
Netherlands
Thank you for joining us!
The First CONCORDIA Workshop on Collaborative DDoS Mitigation was a great success. We look back on an inspiring day with interesting tech talks from research and operations. In an upcoming blog, we will reflect on the workshop and summarise our findings and conclusions; it will be linked here when it is published.
Presentation slides can be found in the agenda. Scroll down for some photos taken during the workshop.
About the Collaborative DDoS Mitigation (CDM) workshop
During this workshop we will give an overview of the state of the art of collaborative DDoS mitigation. We also want to identify bottlenecks and further strengthen the community around this topic. This is important in order to proactively tackle DDoS attacks so that we can minimize disruption to the digital infrastructure of the Netherlands and Europe.
Learning from each other and networking
The workshop consists of presentations, interactive panel discussions and brainstorming sessions and brings together professionals from the DDoS research field and operations teams to learn from each other and network. The evening before the workshop we will organize a networking reception at the workshop venue.
Concluding a research project
The CONCORDIA Workshop on Collaborative DDoS Mitigation concludes our work on the DDoS Clearinghouse in CONCORDIA, a European research project that aims to strengthen Europe’s cyber security capabilities, for example in the areas of generic technologies, specific sectors and education.
The clearing house is currently in a pilot stage and will soon be used in production by the Dutch Anti-DDoS Coalition. For more information on the DDoS clearinghouse, please read one of our recent blogs.
Agenda
September 14th, 2022
| Time | Topic/activity |
|---|---|
| 16:00 | Social drinks / networking at workshop venue |
| 19:00 | End of program at the venue, free to go for dinner in the city centre |
September 15th, 2022
| Time | Topic/activity |
|---|---|
| 09:00 | Drop in, coffee |
| 09:30 | Opening: Introduction, objective, targeted result, agenda Speaker: Cristian Hesselman (SIDN Labs) Slides |
| 09:40 | CONCORDIA introduction Speaker: Christos Papachristos (FORTH) Slides |
| 10:10 | Collaborative DDoS mitigation and the DDoS Clearing house Speaker: Thijs van den Hout Slides |
| 10:30 | Coffee break |
| 11:00 | Tech talk I (operations + mitigation): DDoS mitigation at Cloudflare (tentative title). Speaker: dr. Wouter de Vries (Cloudflare) Slides |
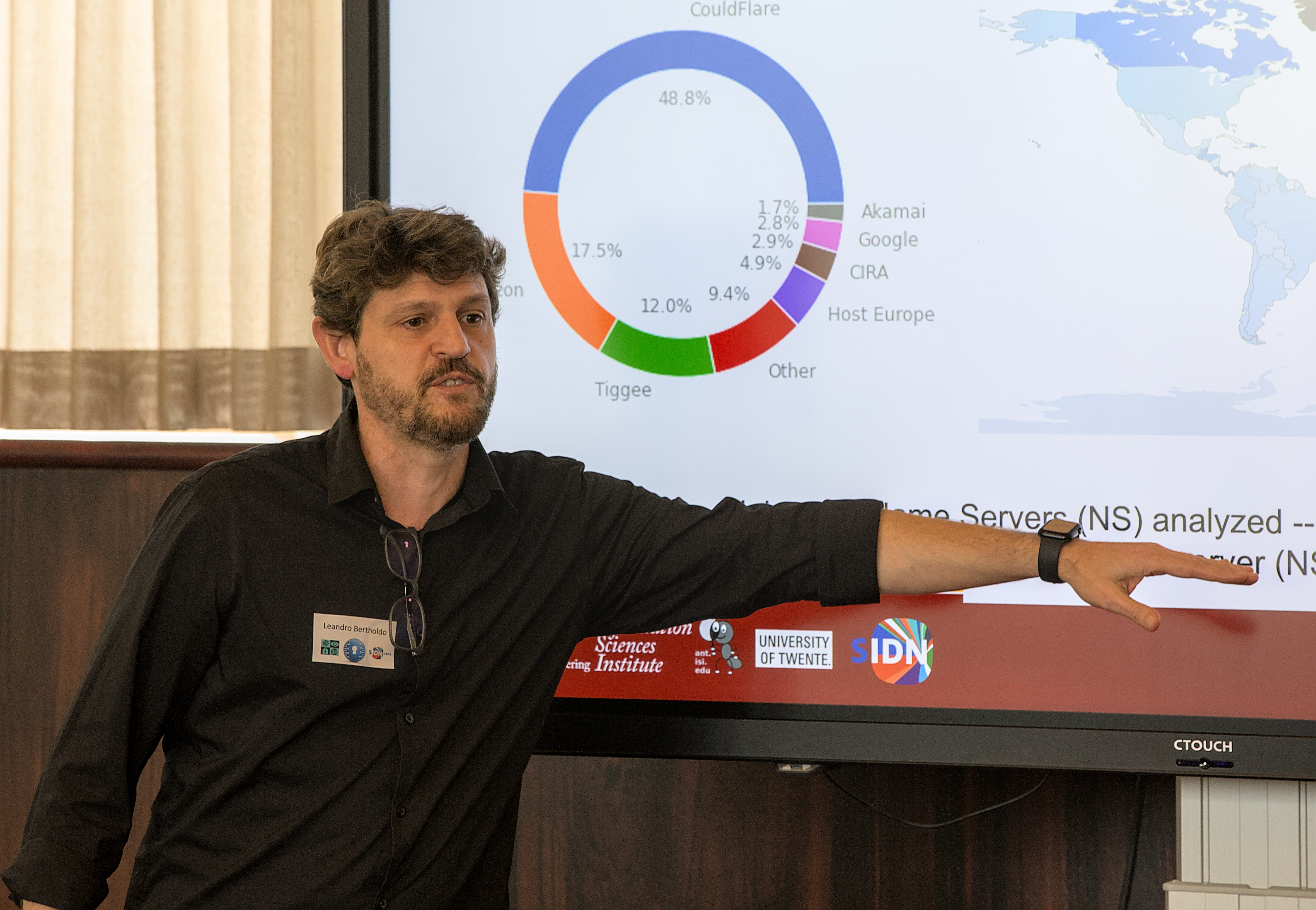
| 11:45 | Tech talk II (measurements + mitigation): Anycast Agility: Network Playbooks to Fight DDoS. Speaker: Leandro Bertholdo (University of Twente) Slides |
| 12:30 | Lunch break |
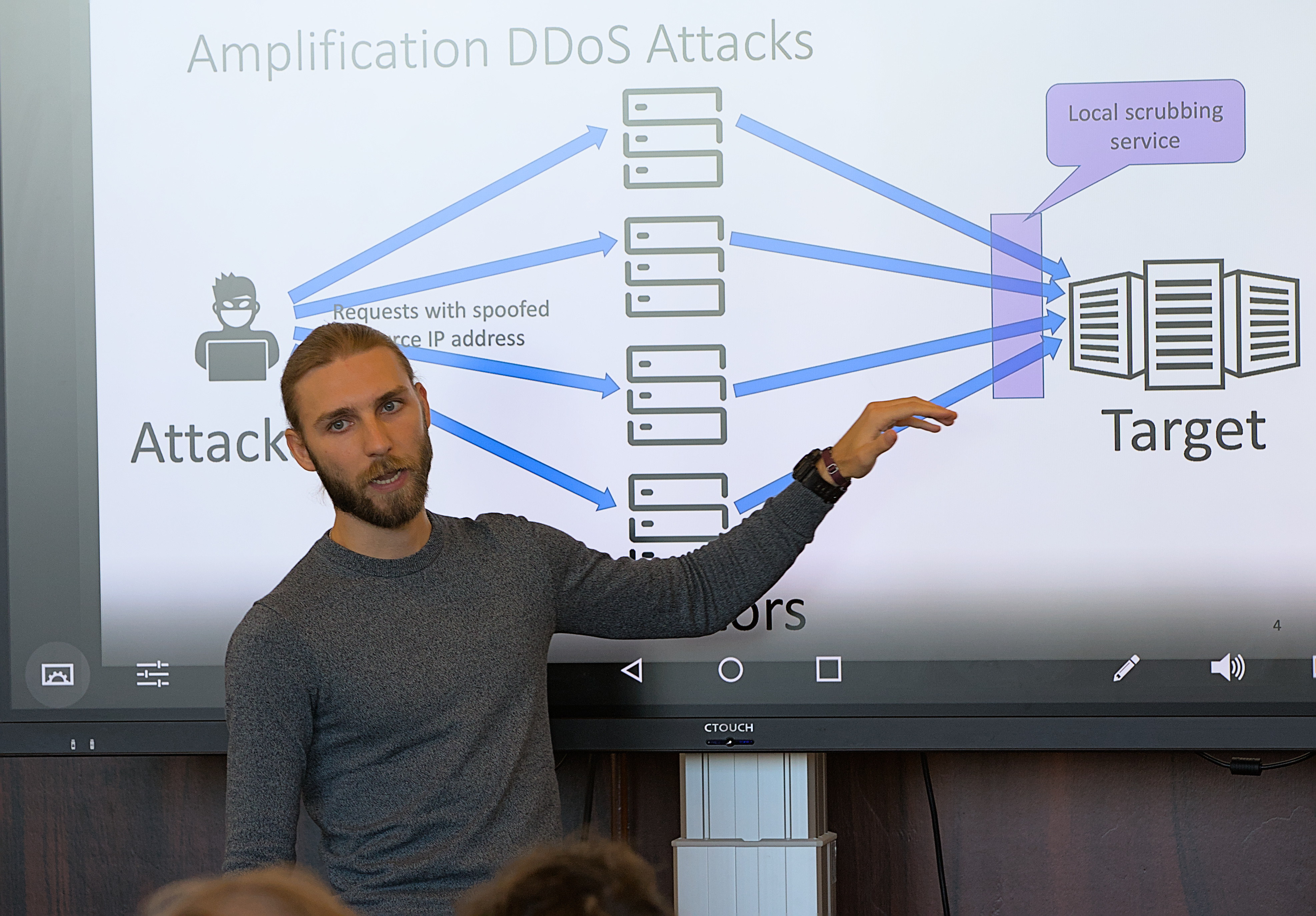
| 13:30 | Tech talk III (measurements + detection): United We Stand: Collaborative Detection and Mitigation of Amplification DDoS Attacks at Scale. Speaker: Daniel Wagner (DE-CIX) Slides |
| 14:15 | Panel: Collaborative DDoS mitigation – where are we now and the way forward Panelists: Jan-Paul Dekker (NL-IX), Karl Lovink (Belastingdienst), Wouter de Vries (Cloudflare), Lili Nemec Zlatolas (University of Maribor) |
| 15:00 | Coffee break |
| 15:30 | Discussion of main takeaways |
| 16:00 | Closing: Possibility to continue networking Speaker: Cristian Hesselman (SIDN Labs) |
Venue
The workshop will be held in Utrecht, The Netherlands. The venue is Villa Jongerius, which is within walking distance from the Utrecht central train station.
Presentation abstracts
DDoS mitigation at Cloudflare
A presentation on how DDoS mitigation is tackled at Cloudflare.
Anycast Agility: Network Playbooks to Fight DDoS
IP anycast is used for services such as DNS and Content Delivery Networks (CDN) to provide the capacity to handle Distributed Denial-of-Service (DDoS) attacks. During a DDoS attack service operators redistribute traffic between anycast sites to take advantage of sites with unused or greater capacity. Depending on site traffic and attack size, operators may instead concentrate attackers in a few sites to preserve operation in others. Operators use these actions during attacks, but how to do so has not been described systematically or publicly. This paper describes several methods to use BGP to shift traffic when under DDoS, and shows that a response playbook can provide a menu of responses that are options during an attack. To choose an appropriate response from this playbook, we also describe a new method to estimate true attack size, even though the operator’s view during the attack is incomplete. Finally, operator choices are constrained by distributed routing policies, and not all are helpful. We explore how specific anycast deployment can constrain options in this playbook, and are the first to measure how generally applicable they are across multiple anycast networks.
United We Stand: Collaborative Detection and Mitigation of Amplification DDoS Attacks at Scale
Amplification Distributed Denial of Service (DDoS) attacks’ traffic and harm are at an all-time high. To defend against such attacks, distributed attack mitigation platforms, such as traffic scrubbing centers that operate in peering locations, e.g., Internet Exchange Points (IXP), have been deployed in the Internet. In this talk, we ask the question: “Is it possible to mitigate more amplification attacks and drop more attack traffic when distributed attack mitigation platforms collaborate?” To answer this question, we collaborate with eleven IXPs that operate in three different regions. We collect network data over six months and analyze more than 120k amplification DDoS attacks. To our surprise, more than 80% of the amplification DDoS are not detected locally, although the majority of the attacks are visible by at least three IXPs. To overcome local detection limitations, we design and evaluate a collaborative architecture that allows participant mitigation platforms to exchange information about ongoing amplification attacks. Our evaluation shows that it is possible to collaboratively detect and mitigate the majority of attacks with limited exchange of information and drop as much as 90% more attack traffic locally.
Contact
If you have any questions about the workshop, don’t hesitate to contact us at thijs.vandenhout@sidn.nl.
Photos
Photos taken by Mattijs Jonker